The Attackers Goal
Collect, encrypt, destroy, or exfiltrate data from an organization for financial or political gain.
The first step in an attack is finding an open door through unpatched software or operating systems, drive by download, 0 day exploits.
Once the attacker has gained access to a system, the next step is to escalate privilege to the local administrator. As a local administrator it is trivial to collect password hashes stored in memory. These hashes are typically any user that has recently logged into the machine. The hashes can then be used to authenticate against other machines in the domain. This lateral movement allows the attacker to break the constraints of the initial breached server or workstation, exposing sensitive data.
Low Hanging Fruit
Many organizations utilize standardized Windows images for building workstations and servers. Many times these windows images contain static passwords for local administrative accounts. These accounts enable attackers the ability to move between servers or computers that utilize the same password or password hash. Once the attacker finds a machine that a domain admin has authenticated on, the entire domain has been compromised.
Prevention
Microsoft has released the LAPs (Local Administrator Password Solution) software package. LAPs automates password rotations and enforces uniqueness across your organizations computers and servers. LAPs is the first line of defense to protect against lateral movement through a network. Thankfully, it is fairly easy to deploy once you understand the basics of how it operates.
- LAPs has a software agent that is installed on each computer it is managing passwords for. The agent MSI can easily be deployed via Group Policy, SCCM, or any other software deployment method.
- LAPs stores passwords in active directory attributes. These attributes require a scheme extension. Additionally, appropriate permissions allow each machine to update it’s passwords, as well as administrative permissions restricting access to password retrieval.
- LAPs uses Group Policy to enforce password policies for machines.
- LAPs will only manage 1 account. Choose wisely.
- LAPs do not keep password history.
Now that you know the basics, let's get LAPs deployed.
- Download LAPs software package from Microsoft.
Once downloaded, place the installer MSI file in a network share accessible from all computers in the planned deployment. Grant 'Domain Computers' read rights on the installer file. - Manually run the installer on your Administrative machine.
Be sure to select all the management tools for install.
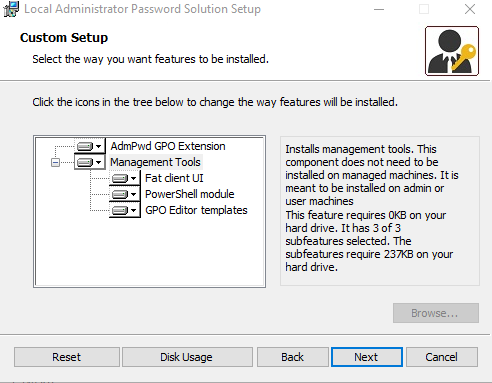
3. Create a new GPO and link it to deploy the LAPs software.
Be sure to link the GPO to the destination OU where you intend to manage machine passwords.
4. Edit your newly created GPO, then browse to:
Computer Configuration > Policies > Software installation.
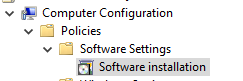
Right click Software installation, and select New > Package.
5. Type the network UNC path location for the MSI installer you downloaded.
Click Advanced, then OK.
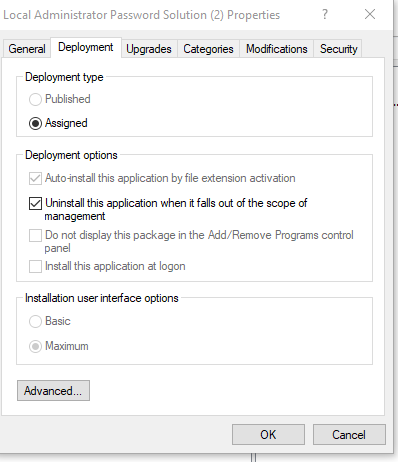
6. On the deployment tab, select 'Uninstall this application when it falls out of scope of management'
then click OK. This ensures that the software is removed when the system is removed from this OU.
7. Add your domain administrative account to the domain group 'Schema Admins'.
This next step will require elevated permissions to complete the schema alterations to Active Directory.
8. Launch a Powershell console using your domain administrative account and run the following commands:
Import-Module AdmPwd.PS
Update-AdmPwdADSchema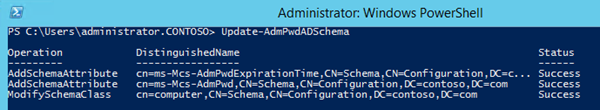
9. We need to add the appropriate permissions in Active Directory to enable each computer to update its own AD attributes (ms-Mcs-AdmPwdExpirationTime and ms-Mcs-AdmPwd).
From powershell console, run the following commands:
Set-AdmPwdComputerSelfPermission -OrgUnit <name of the OU to delegate permissions>This should allow each computer to update its attributes.
10. By default, only Domain Admins have access to read the extended attributes containing the computer passwords.
To add additional groups, run the following command.
Set-AdmPwdReadPasswordPermission -OrgUnit <name of the OU to delegate permissions> -AllowedPrincipals <users or groups>11. Now let's deploy the Group Policy objects to the central store.
On your administrative machine, browse to C:\Windows\PolicyDefinitions and copy file AdmPwd.admx to your central store location
(ex: \\contoso.com\sysvol\contoso.com\Policies\PolicyDefinitions).
Next browse to C:\Windows\PolicyDefinitions\en-US and copy file AdmPwd.adml to your central store location.
(ex: \\contoso.com\sysvol\contoso.com\Policies\PolicyDefinitions\en-US)
12. Create a new GPO to configure the LAPs password policies and link it to the destination OU were you intend to manage machine passwords.
13. Edit your newly created GPO, then browse to:
Computer Configuration > Policies > Administrative Templates > LAPS.
14. Configure the LAPS policy's as desired. Below is a sample.
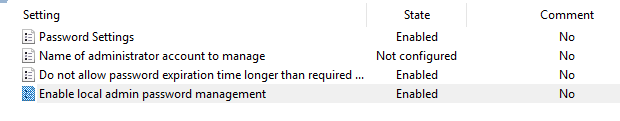
Password Settings
These are the setting used to create passwords within LAPS. Ensure they meet your compliance needs and make adjustments as necessary.
Name of administrator account to manage
This setting only needs to be changed if you are managing an Administrator account that is not using the default well known SID.
Do not allow password expiration time longer than required by policy
Ensures that the password policy configured in LAPS will change the password when the password expires.
Enable local admin password management
Enables LAPS agent to update Active Directory.
15. Run GPUPDATE /FORCE on your target machine.
I recommend a reboot, but it may not be needed.
16. The machine should now be updating it's password according to the GPO you created.
Microsoft has provided two easy ways to retrieve passwords stored in AD. The first is utilizing the LAPS GUI.
LAPS UI App
Type the name of the server and click search.
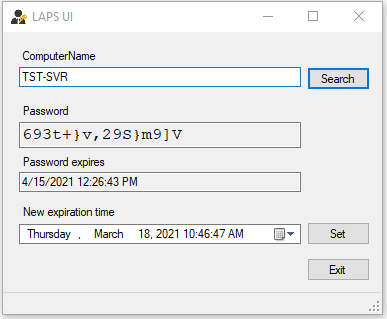
You can also force the machine to reset the password by clicking set. Next time the GPO is applied the LAPS agent will update the password on the server.
LAPS Powershell
To get the password, run the following powershell command:
Get-AdmPwdPassword -ComputerName <computername>To reset the password, run the following powershell command:
Reset-AdmPwdPassword -ComputerName <computername> -WhenEffective <date time>17. One final tidbit, it's important to configure auditing to record events on the Domain Controllers to track who and when someone accessed the machine passwords.
Set-AdmPwdAuditing –OrgUnit: <name of OU on which you want to setup the auditing> -AuditedPrincipals: :<identification of users/groups whose access to password shall be audited>

